It is becoming increasingly common these days for cybercriminals to use hacked versions of Microsoft Office to distribute malware. These versions are offered on popular torrent sites, providing an attractive alternative to paid software. However, the reality is much darker....
Attackers are offering counterfeit versions of various popular software, such as Microsoft's Office, Windows and the Korean Hangul Word Processor. The AhnLab Security Intelligence Center (ASEC) has identified the ongoing "campaign" and analyzed the malware's operation.
What is really happening?
The hacked Microsoft Office installers appear to work reliably, giving users the option to select the correct version and language. However, a hidden .NET malware is running in the background, contacting remote servers to download additional malicious components.
What does this malicious package contain?
- Remote Access Trojan (RAT): These programs give attackers complete control over the victim's computer, allowing them to log keystrokes, access the webcam and record the screen, for example.
- Cryptocurrency miners (XMRig): These software programs use the computer's resources to mine Monero, which can cause significant system slowdowns.
- Proxy devices (3Proxy): These programs turn the infected system into a proxy server, allowing attackers to route malicious traffic through it.
- Malware downloaders (PureCrypter): These download and install additional malware, ensuring that the system remains infected.
- Anti-virus bypass (AntiAV)A: These programs disable or interfere with existing security software so that it cannot detect and remove malware.
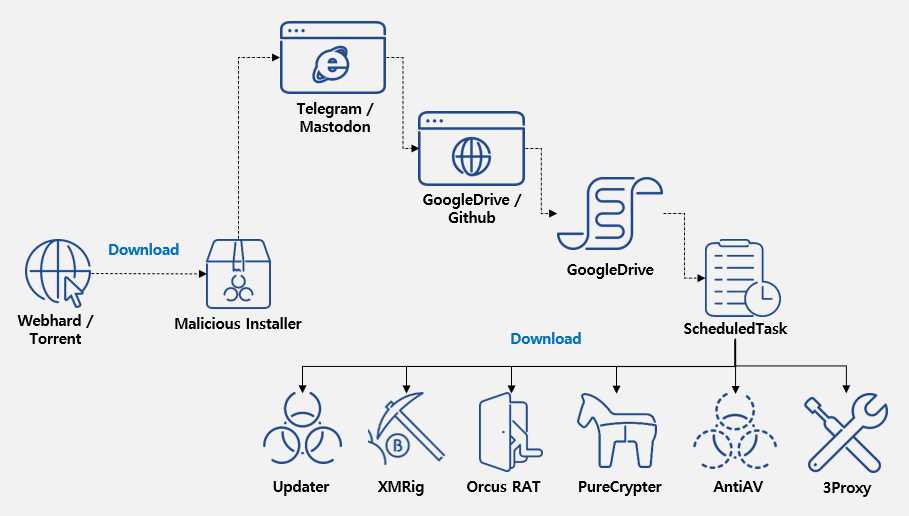
Since these files are not digitally signed and users are willing to ignore antivirus warnings when they are run, they are often used to infect systems with malware, in this case a nice big bundle of viruses.
Using pirated software may seem attractive in the short term, but the risks far outweigh the benefits. Readers interested in the world of IT and tech should bear in mind that security is one of the most important considerations in the digital space. Be vigilant and avoid the dangers of pirated software.


